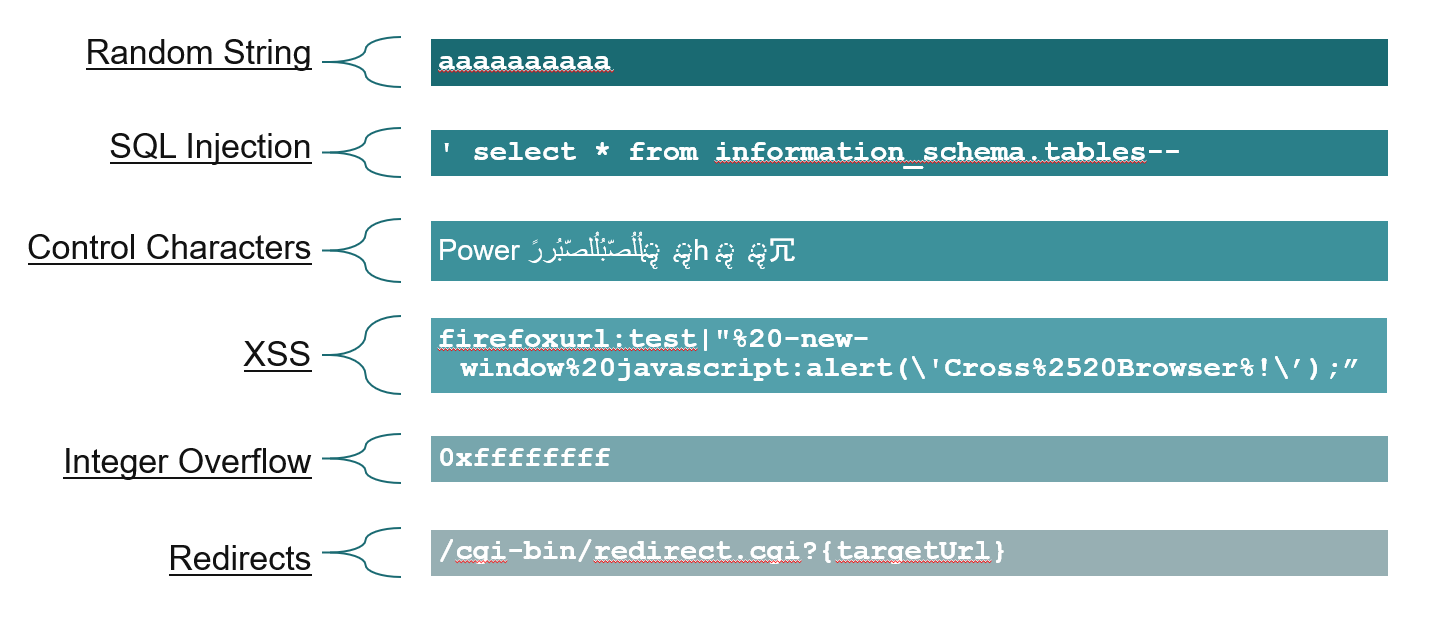
Fuzz testing, a technique traditionally associated with desktop software and embedded systems, is becoming increasingly valuable for online services and web applications. By bombarding systems with unexpected, random, or malformed inputs, fuzz testing can uncover edge cases and vulnerabilities that more structured testing approaches might miss.
What is Fuzz Testing?
At its core, fuzz testing involves providing invalid, unexpected, or random data as inputs to a software system. The goal is to expose:
- Crashes and memory leaks
- Input validation failures
- Unhandled exceptions
- Security vulnerabilities
- Race conditions and concurrency issues
While unit and integration tests verify that software works correctly under expected conditions, fuzz testing reveals how it behaves under unexpected conditions.
Why Fuzz Testing Matters for Web Services
Online services face unique challenges that make fuzz testing particularly valuable:
- Exposure to the public internet: Web services are directly accessible to potential attackers
- Diverse client implementations: Services must handle requests from many different clients with varying behaviors
- Continuous deployment: Frequent updates increase the risk of introducing vulnerabilities
- Distributed systems complexity: Interactions between microservices create more potential failure points
Implementing Fuzz Testing for Web Services
API Fuzzing
Modern web services expose APIs that can be systematically fuzzed:
- Test with malformed JSON/XML structures
- Inject invalid values and extreme edge cases
- Mix valid and invalid parameters
- Manipulate authentication tokens
- Send requests with missing or additional headers
Traffic Replay with Mutation
A powerful approach for existing services:
- Capture real production traffic
- Modify requests in various ways (mutation)
- Replay the modified traffic against test environments
- Monitor for unexpected behaviors
Chaos Engineering
Extend fuzzing beyond inputs to infrastructure:
- Simulate service outages
- Introduce network latency or packet loss
- Exhaust resources (memory, connections, etc.)
- Add random delays to system calls
Getting Started with Fuzzing
Begin with these practical steps:
- Start small: Focus on critical endpoints or services
- Define clear success criteria: Know what constitutes a failure
- Isolate your testing environment: Ensure fuzz tests can't affect production
- Build good observability: You need to detect when things go wrong
- Automate response to failures: Capture enough information to reproduce issues
Tools for Web Service Fuzzing
Several tools can help implement fuzzing for web services:
- Generic fuzzers: American Fuzzy Lop (AFL), libFuzzer
- API-specific tools: RESTler, Swagger Fuzzer
- Protocol fuzzers: HTTP, WebSocket, and gRPC fuzzers
- Chaos engineering platforms: Chaos Monkey, Gremlin
Conclusion
Fuzz testing is no longer just for traditional software applications. By incorporating fuzzing into your testing strategy for online services, you can discover and address edge cases and vulnerabilities before they affect users in production. As with any testing approach, the key is to start simple, learn from the results, and gradually increase sophistication.